What’s Needed to Secure the Software Supply Chain
- Increased dependency on third-party codes for building software applications has exposed several vulnerabilities in the software supply chain.
- To secure these software supply chains, enterprises need end-to-end visibility of the development lifecycle.
- Enterprises must also act proactively and develop a comprehensive risk management framework.
May 23, 2025 |
Software development is today highly fragmented and decentralized, with many companies using third-party components for software development. Even companies that develop their own software often leverage third-party and open-source software for services and support.
Most software applications are now made up of several open-source components and libraries, which inherit functionality from third-party sources.
While such an arrangement allows developers to use preferred tools and release functional software to their users quickly, it also exposes businesses and their customers to vulnerabilities that are outside their direct control.
Not surprisingly, there have been several recent instances of malicious players gaining unauthorized access to company systems and data.
Risks in the Software Supply Chain
The software supply chain is a large, complex and interconnected system of technology, people and process touchpoints. These touchpoints pose several risks and are vulnerable to security threats.
Software supply chain attacks have become more frequent as well as sophisticated. An attacker may use advanced malware that can change its form to evade detection. Attackers may also evade traditional security measures by injecting malicious code that is hard to distinguish from normal code.
Clearly, these intrusions have become increasingly difficult to detect.
Here are the common threats in the software supply chain:
1. Known vulnerabilities:
Third-party components often come with unintended vulnerabilities. Many of these are known and publicly tracked in the Common Vulnerabilities and Exposure (CVE) list. Software component analysis can identify a given code and associate it with known CVEs by cross checking the metadata of the software with public databases.
2. Unknown vulnerabilities:
Coding mistakes such as logic flaws and poor encryption can make an application vulnerable to malicious attacks. Such errors can remain undetected in first as well as third-party code for a long time. Most of these flaws can be identified with static code analysis and dynamic code review tools.
3. Embedded malicious code:
Intentional threats from external injection are often disguised as an already validated component. These threats are the most difficult to detect and can do a lot of damage. Attackers can infect the affected endpoints with malicious software and circumvent the authentication controls in this process. They can also inject malicious code into a file or entire package that an end-user intends to run on their systems.
Also Read: How to Solve High-Tech Supply Chain Challenges
How to Secure the Software Supply Chain
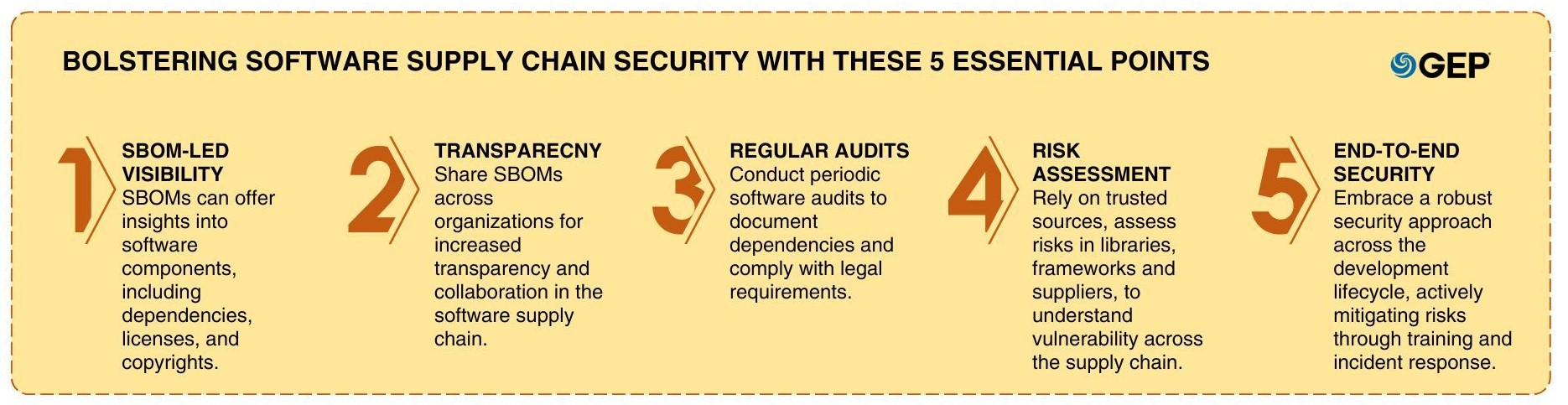
At the outset, businesses need full visibility into the components of their software. This can be achieved with a software bill of materials (SBOM) that lists all third-party components and dependencies within the software. This document has machine-readable data to help identify all contents of a software package. Additionally, it includes license data and copyrights of all components used in the software.
SBOMs can be shared across various organizations that use software components. This helps to promote transparency across the software supply chain.
In addition to visibility, enterprises also need to periodically audit their software supply chains. They can do this by maintaining a clear record of all their software dependencies.
Following the recent attacks that affected several government agencies, the U.S. federal government has made software audits a legal requirement for every company selling software to a government agency.
Next, businesses must only use trusted repositories and verified sources and conduct regular risk assessment of libraries, frameworks and suppliers. Beyond merely identifying vulnerabilities and security issues, enterprises also need to understand their context to be able to determine the true risk. This is why they cannot rely on separate point solutions that fail to analyze the full context of a risk within the entire supply chain.
When a new vulnerability is discovered, enterprises must check first to determine whether they are impacted. In case they are, update to obtain the latest security patches and functionality.
Along with complete visibility, organizations need end-to-end vigilance to fully secure their software supply chains. This requires going through the proprietary code development, compiling and interim builds even before the developer calls an external package. It requires vigilance throughout the development process and lifecycle all the way to release, distribution, production, deployment and even afterward.
Instead of looking at isolated points in the pipeline, a comprehensive security solution can connect the dots between different issues and security findings. In doing so, it can enable consistent oversight, monitoring and mitigation in development as well as production environments.
In other words, the end-to-end security solution can act holistically on the software supply chain and allow enterprises to address risks by acting on a large scale.
Finally, enterprises must adopt a proactive approach and develop a comprehensive risk management framework. They should assess possible breach scenarios beforehand as well as organizational readiness to swiftly respond and mitigate the impact.
Train employees across different teams on how to respond to a security breach. Enterprises must also have a dedicated incident response team and well-documented procedures to be followed in case of a breach.
Overall, by fostering end-to-end visibility and taking action to monitor and mitigate potential risks, enterprises can build and maintain resilient software supply chains.
Learn how GEP can help to secure your supply chain.