
Why the NPM Attack Is a Wake-Up Call for Software Supply Chains
- Hundreds of popular JavaScript packages were compromised recently, in a sophisticated attack that spread automatically through the software supply chain.
- Hackers stole developer credentials to break into corporate infrastructure, using a self-replicating worm to maximize damage.
- Supply chain teams have to go beyond basic security checks and start rotating credentials, isolating dependencies and monitoring their vendor ecosystem continuously.
October 21, 2025 | Supply Chain Risk Management 5 minutes read
The software supply chain has long been a security weak point. In September 2025, this risk became catastrophic. A massive attack injected malicious code into hundreds of widely used open-source JavaScript packages, targeting the foundation of modern software development globally.
The attack exploited the industry's deep trust in open-source code, bypassed traditional security measures and introduced a self-propagating worm into the software build process. This isn’t just a technical problem for IT. It's a critical business risk for every organization that uses software. What can supply chain teams do to mitigate the risk?
What Is the NPM Supply Chain Attack?
Node Package Manager (npm) is the world's largest registry for JavaScript code. When developers build applications, they typically pull in thousands of pre-built, open-source "packages" from npm. The problem: every package installed introduces trust in its original author and all the other packages it relies on.
A software supply chain attack is like compromising a factory that makes brake pads. You inject a defect at the source, so it gets distributed to every downstream user.
In this attack, threat actors launched a targeted phishing campaign to compromise the accounts of several key npm package maintainers. Once they had control of these trusted accounts, they published malicious versions of incredibly popular utilities. Some get downloaded over 2.6 billion times per week. A single compromised account became a vector for global infection.
Tracing the NPM Supply Chain Attack Timeline
The speed with which the attack propagated itself underscores the narrow window businesses have to detect and respond to modern supply chain threats.
• Initial Compromise (September 2025)
It started with phishing emails. Hackers targeted npm maintainers with convincing fake login pages. Some even mimicked multi-factor authentication screens. The maintainers had no reason to suspect anything. They entered their credentials, and the attackers had their keys.
• Malicious Deployment
Once inside, the attackers pushed malicious code into at least 18 popular packages. These weren't obscure tools, but the packages millions of developers rely on every day. The bad versions stayed live for just a few hours, but that was enough to potentially hit millions of developers and corporate cloud environments.
• The Worm Emerges
Researchers discovered a self-replicating worm called "Shai-Hulud" spreading through the npm ecosystem. Unlike a typical attack where someone has to manually push each payload, “Shai-Hulud” reproduced on its own, infecting more packages without anyone directing it.
• Rapid Response
The good news: security teams caught it and cleaned it up fast. Most compromised packages were gone within hours. But here's the problem that kept security experts up at night: from initial breach to global impact took only minutes. Not days. Minutes.
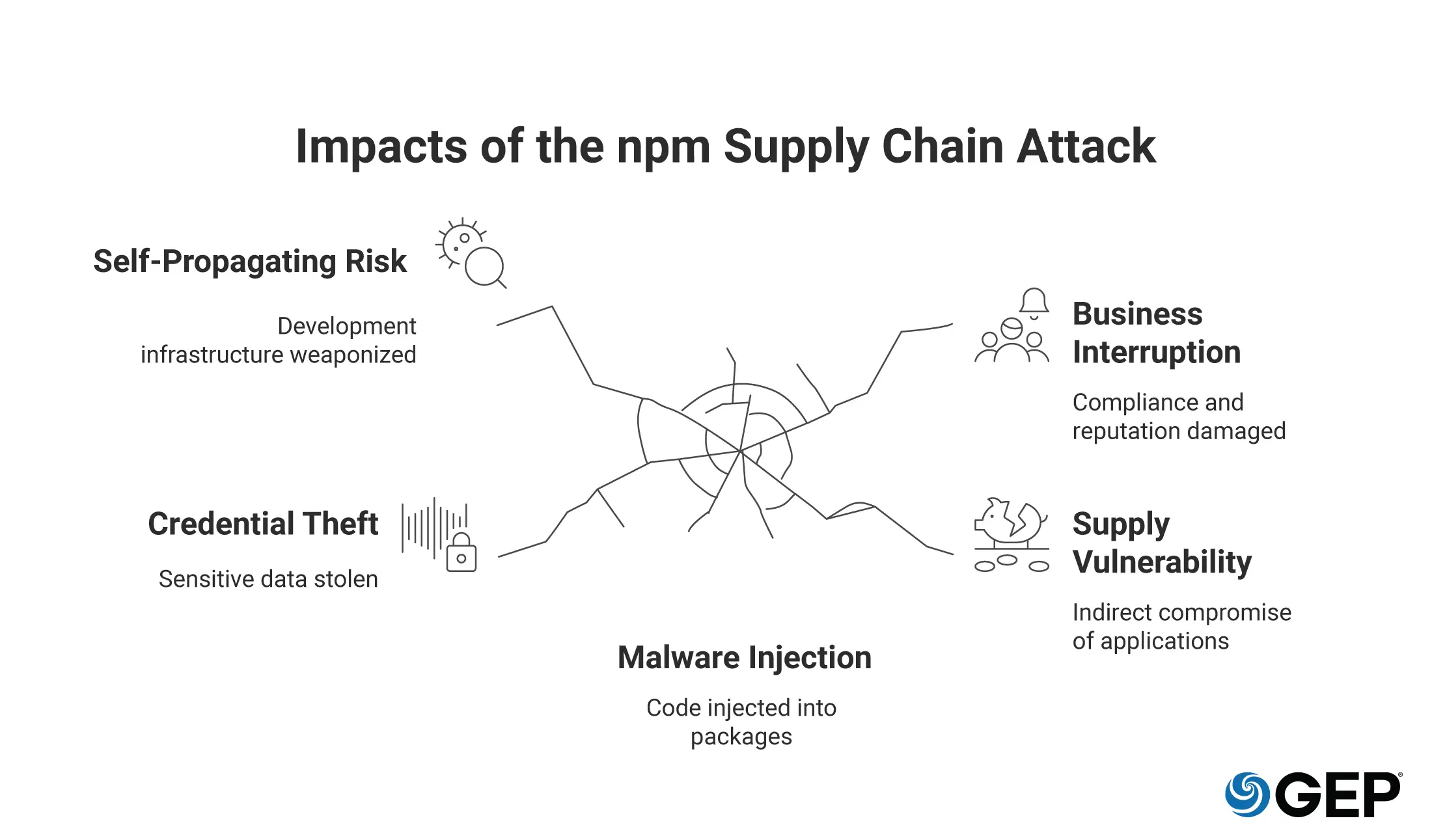
The Impact: Widespread, Subtle and Far-Reaching
While the malware's immediate objective was stealing cryptocurrency, the method of attack presents far greater threats, such as:
• Credential Theft and Cloud Compromise
The malware scanned developer environments for sensitive credentials, including GitHub tokens, npm tokens, SSH keys, and cloud service provider keys (AWS, Google Cloud, Azure). If found, attackers could move from a developer's laptop directly into the company's cloud infrastructure, leading to data theft, ransomware or deletion of production environments.
• Self-Propagating Risk
The worm used stolen credentials to inject code into other packages the compromised developer maintained, creating a self-reinforcing chain reaction. The worm didn't stop at a single infection either. It actively weaponized the victim's development infrastructure for ongoing espionage.
• Business Interruption and Compliance
If attackers accessed an organization’s personal, financial or regulated data, that organization is required to notify those impacted. The mere presence of compromise can trigger contractual breaches with customers and vendors, resulting in indemnity claims and severe reputational harm.
• Supply Chain Vulnerability
Every third-party software component introduces potential risk. An attack on a dependency your company doesn't use directly can still compromise applications if one of your vendors uses it.
Why Basic Hygiene Alone Isn't Enough
Traditional cybersecurity focuses on scanning known vulnerabilities or viruses. This attack bypassed those defenses by exploiting trust. Attackers stole a trusted person's key and used the legitimate publishing mechanism to distribute malware. This means that:'
• Code Was "Clean" on Arrival
The malicious packages were published from valid, trusted npm accounts. They would sail through automated checks that verify the publisher's authenticity, not the code's content.
• Automation Was the Weapon
The attack leveraged the same automation developers rely on, like post install scripts and automatic dependency updates, to ensure the malicious code executed immediately and spread automatically.
• Vetting Is Insufficient
For many organizations, vetting thousands of packages in the npm ecosystem is impossible. You might vet one version of a package, only for the next compromised version to be pulled in by an automated update.
These factors demand that enterprises now assume that any code pulled into their build environments could be hostile and design their systems to neutralize it.
Immediate Actions for Supply Chain Security Teams
Procurement and supply chain professionals must act swiftly and decisively. Some advantageous steps based on isolating threats include:
• Enforce Mandatory Credential Rotation
Immediately rotate all developer credentials, including cloud keys, GitHub tokens, and npm tokens. This is the single most effective way to cut off the worm's ability to propagate.
• Audit and Pin Dependency Versions
Use Software Composition Analysis tools to identify which applications use compromised versions. Then, take measures to prevent automatic pulling of unverified updates.
• Block Automatic Scripts by Default
Many of these attacks work by running malicious code automatically when a new software component is installed. Use tools that block this behavior from the start.
• Isolate Your Build Process in a Sandbox
Create a digital "sandbox" for building software. This isolated environment, like a virtual machine, should be walled off from everything that matters: corporate credentials, sensitive parts of your network, and developers' local files.
• Introduce a "Cooling-Off" Period for Updates
Configure your systems to wait about a week before adopting new package versions. That way, you let the broader developer community find any hidden dangers first.
• Require Phishing-Proof Logins
Protect your high-value accounts by requiring phishing-resistant multi-factor authentication (MFA), such as physical security keys. It's one of the most effective ways to shut down an attacker's easiest entry point.
Build a More Resilient Supply Chain
Learn How AI-Powered Orchestration Drives Real-Time Risk Management
A Watershed Moment for Business Risk
Modern threats like the NPM attack aren't just about breaking into a perimeter. They're about compromising the components you willingly invite in.
For organizations to remain resilient, they must be proactive in defending against these threats. Procurement, compliance and supply chain teams are now on the front lines, tasked with setting security standards for every piece of software the organization deploys.
Discover More: Supply Chain Software
Implementing Zero Trust, mandating isolation and embracing continuous monitoring are critical steps for companies to guard their software supply chains against the inevitable next attack.



